As businesses are more reliant on digital connectivity, social engineering is thriving. This blog looks a little more at social engineering and how to protect yourself from it.
Any security expert will tell you that the weakest link in the security chain is the individual who accepts a person or scenario at face value.Therefore, if you let someone into your business who claims they’re the plumber or delivery guy without checking legitimacy first, then you’re exposing yourself to whatever risk he may represent. This is true no matter how many cameras or security guards you have.
The same is true for online activity. How do you check that the website you’re using is genuine or safe for you to provide your information? How do you know that the person you’re emailing is who they say they are, and aren’t sending you emails with harmful attachments? it’s important to understand the red flags when it comes to social engineering online.
What is social engineering?
Social engineering is the act of manipulating a person to divulge their private information, usually through digital communication. It is the term used for a range of malicious activities that trick users into making security mistakes and giving access to protected systems. Most hackers are master manipulators, but that doesn’t mean just manipulators of technology whereas some cybercriminals prefer to use human manipulation. Social engineering relies on the basic human instinct of trust to steal data and commit cybercrime.

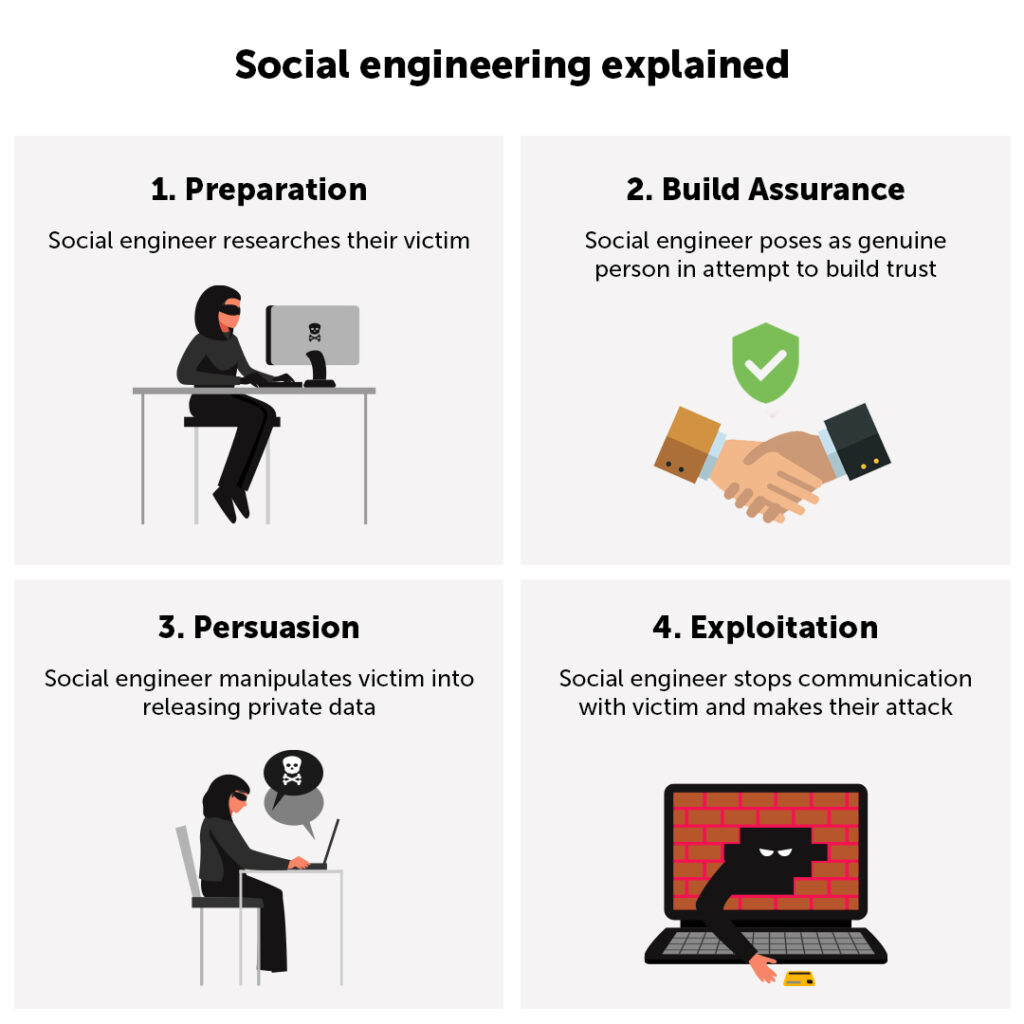
How social engineering works
Social engineering explained:
- Preparation: The social engineer researches their victim and pulls together information about them using social media and the internet etc…
- Build assurance: The social engineer poses online as a legitimate genuine person and builds trust with their victim (e.g., an IT professional requesting information to fix a security gap on a device).
- Persuasion: The social engineer manipulates the victim into giving them the confidential information that they desire, such as account logins and contact information.
- Exploitation: The social engineer stops communication and uses the data to commit their attack.
Know the red flags
A social engineer can pose as a person you trust
Whether it’s a friend, a co-worker, a manager or banking institution – if you receive a suspicious message or email containing links or downloads, be sure to ask them about it first before clicking anything.
The request is urgent
A social engineer doesn’t want you to think about or consider their tactics. That’s why many attacks involve some type of urgency. For example, an urgent request for you to download security software to remove a virus off your computer.
You feel that it’s too good to be true
Have you ever received an email saying you’ve won the lottery or a free holiday? The chances are that if it seems too good to be true, it often is just that, and probably a social engineering attack.
The sender can’t provide proof of their identity
If you feel suspicious, raise your concerns to the person who may be engaging in social engineering, If they’re unable to prove their identity, perhaps they won’t do a video call with you, chances are they can’t be trusted. We recommend trying to contact the person through a different medium to the original message.
Examples and types of social engineering
Scareware – Malware that is intended to scare you into taking action . For example, emails and pop-ups saying “act now” to get rid of a virus on your device.
Email phishing – The delivery of a malicious link, download or attachment via email (often seems legit and familiar).
Baiting – Disguising malware in the form of something desirable however this often occurs on social media whereby someone encourages you to download music or a video file that is infected with malware.
Physical breaches – For example, a social engineer posing as an IT person could arrive at your office with a request to update employee devices – they may actually do this. However, at the same time they will place a keylogger/tracker onto the devices to exploit in future cyberattacks.
DNS spoofing – This is also known as cache poisoning. Meanwhile DNS spoofing is when a browser is manipulated so that users are redirected to toxic websites.
Tips to protect yourself from social engineering attacks
The best defence against a social engineer is to educate yourself on the risks and be aware of the red flags. You can stop social engineering attacks in their tracks by simply being hesitant, and taking the time to approach almost all online interactions with apprehension.
- Don’t click on unfamiliar links
- Be wary when it’s too good to be true
- Don’t overshare personal information online
- Use multi-factor authentication where possible
- Use complex and lengthy passwords and change them regularly
- Be vigilant and question friends if their messages seem sceptical
- Contact sources via a different channel or medium
Want to know more about security awareness and best practices?
848 is a trusted IT partner with 11 years of experience in configuring, scaling and securing cloud-first solutions. Our team of cyber security experts can help you and your business defend against malicious cyberattacks and cyber criminal’s tactics.